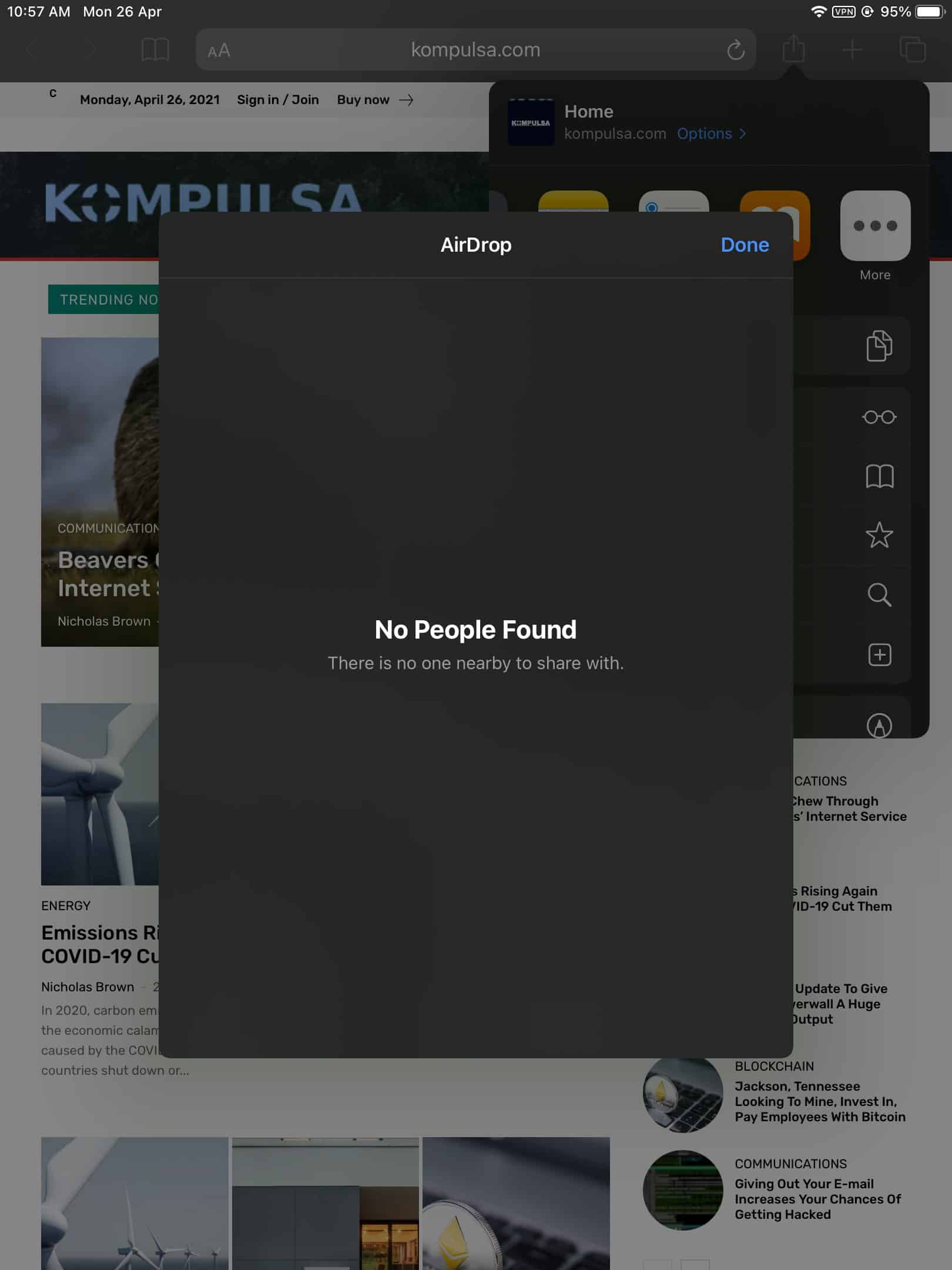
AirDrop — a sharing feature included in all Apple phones, tablets, and computers has a vulnerability, according to the German university Technische Universitat Darmstadt. The security vulnerability may expose users’ phone numbers and email addresses if they bring up their sharing panel on their Mac OS or iOS devices.
According to the research, the vulnerability could expose your phone number/email even to strangers within range of your device (this means devices within your Bluetooth and Wi-Fi range). This was attributed to a vulnerability in the hashing functions that obfuscate users’ phone numbers/emails.
“As an attacker, it is possible to learn the phone numbers and email addresses of AirDrop users – even as a complete stranger. All they require is a Wi-Fi-capable device and physical proximity to a target that initiates the discovery process by opening the sharing pane on an iOS or macOS device,” Secure Mobile Networking Lab (SEEMOO) and the Cryptography and Privacy Engineering Group (ENCRYPTO) said in a press release.
In this day and age personal information (especially unique identifiers such as email, which link you to your online activities and can get you hacked) is desperately sought after by criminals and corporations alike. That means that this vulnerability needs to be nipped in the bud as quickly as possible.
To protect yourself, you can turn AirDrop off for now by bringing up the Control Center, tap and hold the square with the Wi-Fi and Bluetooth icons in it, then tap AirDrop > Receiving Off. Or you can avoid bringing up the sharing panel when in public places, since that is when your details are exposed.